If your customers have been asking for your SOC 2 report and you’re unsure how to obtain this compliance certification, don’t worry; we’ve got you covered! This blog will guide you through the process of achieving SOC 2 compliance, allowing you to assure prospective customers that the data they share with you will be protected at all costs.
To get started, it’s essential to understand the SOC 2 Trust Services Criteria (TSC), which form the foundation of the SOC 2 framework.
Asking the Right Questions
When reviewing the SOC 2 Trust Services Criteria, consider your customers’ perspectives:
- What type of data are they entrusting to you? Is it personally identifiable, confidential, or private?
- Are they concerned about system availability and uptime?
- Do they prioritize privacy and confidentiality?
- Is their primary concern the security of the data?
Every SOC 2 report must include the Security category, as it serves as the baseline for the other four criteria. The remaining categories—Availability, Confidentiality, Processing Integrity, and Privacy are optional but highly recommended based on your business model and customer expectations.
Many businesses start with the Security criterion for their first SOC 2 audit and then expand to include other areas like Availability and Confidentiality in future audits.
An Overview of the Five Trust Services Criteria

SOC 2 compliance revolves around five key principles known as the Trust Services Criteria:
- Security
- Availability
- Confidentiality
- Processing integrity
- Privacy
Each of these criteria outlines specific needs that must be met for compliance.
Here’s a brief description of the categories:
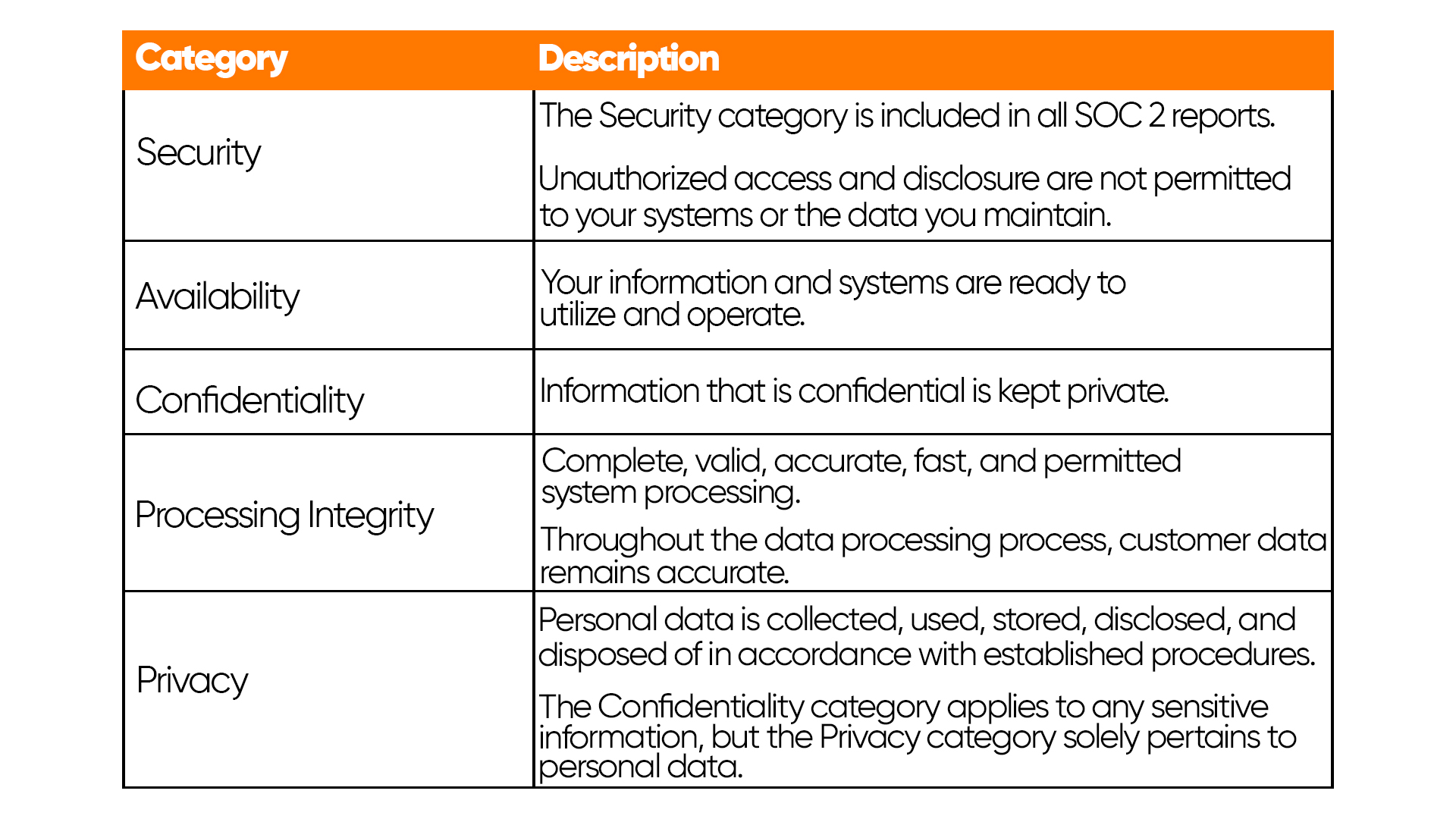
Each category is broken down into multiple criteria that have to be met by the controls that your organization puts into practice.
Understanding the SOC 2 Trust Services Criteria for Compliance
To achieve SOC 2 compliance, your organization must align with one or more of the five SOC 2 Trust Services Criteria: Security, Availability, Confidentiality, Processing Integrity, and Privacy. Here’s a quick breakdown:
Security
Security is the core criterion and must be included in every SOC 2 report. It focuses on protecting systems that process, store, and transmit data from unauthorized access, errors, or breaches. Controls are put in place to help detect and prevent issues such as system failures or data theft.
Availability
Availability refers to whether your systems and services are accessible as expected. If customers are concerned about uptime, service-level agreements (SLAs), or system status, including this criterion is essential. Controls typically involve performance monitoring, backups, and disaster recovery plans.
Confidentiality
This criterion covers the protection of sensitive business data from collection through to destruction. If clients request non-disclosure agreements (NDAs) or data deletion after contract termination, confidentiality becomes a priority. It ensures that only authorized individuals can access classified information.
Processing Integrity
Processing integrity ensures that your system processes data accurately and completely. This is crucial if you run a platform that handles transactions or data flows (such as payment processing). While less common, it is vital in industries that depend on data accuracy.
Privacy
Privacy governs how you collect, use, retain, and share personal data. If your product handles identifiable client information like names, health records, or social security numbers, you should include it. GDPR compliance may cover similar ground.
Choosing the right SOC 2 Trust Services Criteria depends on your product and your customers’ needs.
How to Choose the Right SOC 2 Trust Services Criteria for Your Business
Choosing the right Trust Services Criteria for your SOC 2 compliance audit can feel overwhelming, but it ultimately comes down to the services you offer and what your customers care about most.
Let’s break this down with some relatable examples:
HR SaaS Products
If your platform helps companies manage hiring workflows and stores sensitive information like resumes and interview notes, confidentiality should be a top priority. Clients will want assurance that their candidates’ data is secure, and this criterion helps you demonstrate your commitment to protecting their information.
DevOps or CI/CD Tools
If you provide infrastructure tools for developers to build and deploy code, availability is likely your top priority. Even a minor downtime can hinder deployments and delay updates. Including availability in your SOC 2 scope shows that you have strong system monitoring and uptime controls in place.
Fintech and Payment Platforms
When handling financial transactions or user payment data, processing integrity is critical. Customers need to trust that every transaction is processed accurately and promptly. This criterion demonstrates that your systems are reliable and capable of catching and correcting errors quickly.
Conclusion
Achieving SOC 2 certification isn’t solely about meeting technical requirements; it’s about building customer trust through robust data protection and well-documented security controls. Selecting the right Trust Services Criteria ensures your SOC 2 report reflects what truly matters to your users. Start with Security—it’s mandatory and foundational.
Security, AI Risk Management, and Compliance with Akitra!
In the competitive landscape of SaaS businesses, trust is paramount amidst data breaches and privacy concerns. Akitra addresses this need with its leading AI-powered Compliance Automation platform. Our platform empowers customers to prevent sensitive data disclosure and mitigate risks, meeting the expectations of customers and partners in the rapidly evolving landscape of data security and compliance. Through automated evidence collection and continuous monitoring, paired with customizable policies, Akitra ensures organizations are compliance-ready for various frameworks such as SOC 1, SOC 2, HIPAA, GDPR, PCI DSS, ISO 27001, ISO 27701, ISO 27017, ISO 27018, ISO 9001, ISO 13485, ISO 42001, NIST 800-53, NIST 800-171, NIST AI RMF, FedRAMP, CCPA, CMMC, SOX ITGC, and more such as CIS AWS Foundations Benchmark, Australian ISM and Essential Eight etc. In addition, companies can use Akitra’s Risk Management product for overall risk management using quantitative methodologies such as Factorial Analysis of Information Risks (FAIR) and qualitative methods, including NIST-based for your company, Vulnerability Assessment and Pen Testing services, Third Party Vendor Risk Management, Trust Center, and AI-based Automated Questionnaire Response product to streamline and expedite security questionnaire response processes, delivering huge cost savings. Our compliance and security experts provide customized guidance to navigate the end-to-end compliance process confidently. Last but not least, we have also developed a resource hub called Akitra Academy, which offers easy-to-learn short video courses on security, compliance, and related topics of immense significance for today’s fast-growing companies.
Our solution offers substantial time and cost savings, including discounted audit fees, enabling fast and cost-effective compliance certification. Customers achieve continuous compliance as they grow, becoming certified under multiple frameworks through a single automation platform.
Build customer trust. Choose Akitra TODAY! To book your FREE DEMO, contact us right here.
FAQs
How Do I Choose the Right SOC 2 Trust Services Criteria ?
Choose based on your product. For example, pick Confidentiality if you handle sensitive data, or Availability if uptime matters to your users.
Is Privacy Required in SOC 2 if I Follow GDPR?
Not always. GDPR compliance may cover Privacy, but confirm with your auditor to be sure.











